SeCloak: ARM TrustZone-based Mobile Peripheral Control
ABOUT
SeCloak provides users with secure, "virtual" switches to control peripherals on their smart devices by providing a small, OS-agnostic enforcement layer that mediates untrusted accesses to devices.
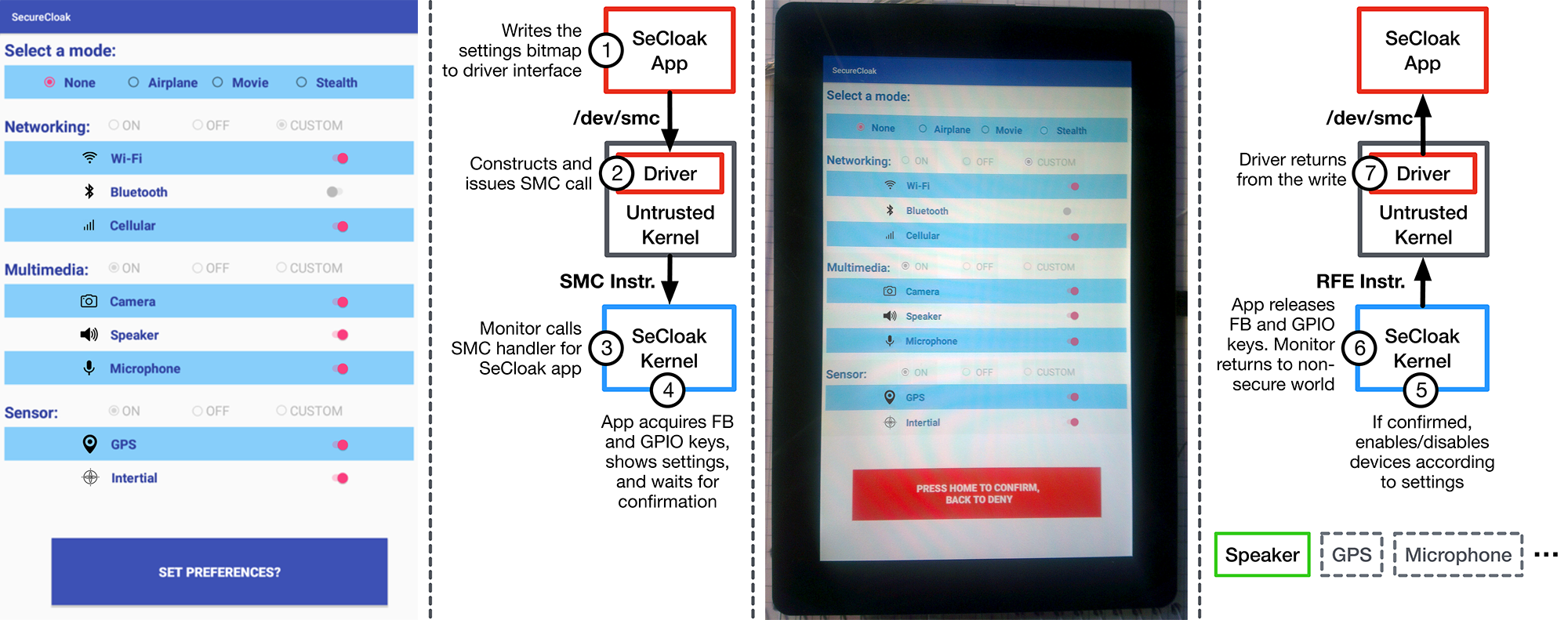
Figure: Overview of the SeCloak workflow. The leftmost panel shows the untrusted SeCloak app. The second panel shows the steps after the user presses the "Set Preferences" button. The third panel shows a photograph of the SeCloak secure kernel, which (re-)displays the settings to the user and waits for user confirmation. The fourth panel shows the steps taken if the user confirms the settings, such as disabling/enabling devices.
PUBLICATIONS
SeCloak: ARM TrustZone-based Mobile Peripheral Control
Matthew Lentz, Rijurehkha Sen, Peter Druschel, Bobby Bhattacharjee
MobiSys 2018 (International Conference on Mobile Systems, Applications, and Services)
Paper
Slides
Show Abstract
Reliable on-off control of peripherals on smart devices is a key to
security and privacy in many scenarios. Journalists want to reliably turn
off radios to protect their sources during investigative reporting. Users
wish to ensure cameras and microphones are reliably off during private
meetings. In this paper, we present SeCloak, an ARM TrustZone-based
solution that ensures reliable on-off control of peripherals even when the
platform software is compromised. We design a secure kernel that co-exists
with software running on mobile devices (e.g., Android and Linux) without
requiring any code modifications. An Android prototype demonstrates that
mobile peripherals like radios, cameras, and microphones can be controlled
reliably with a very small trusted computing base and with minimal
performance overhead.
Hide Abstract
RESOURCES
Source Code - Secure Kernel @Github
PEOPLE
 Bobby Bhattacharjee
Bobby Bhattacharjee
 Peter Druschel
Peter Druschel
 Matthew Lentz
Matthew Lentz
 Rijurekha Sen
Rijurekha Sen

